Microfluidic Mechanoporation Device
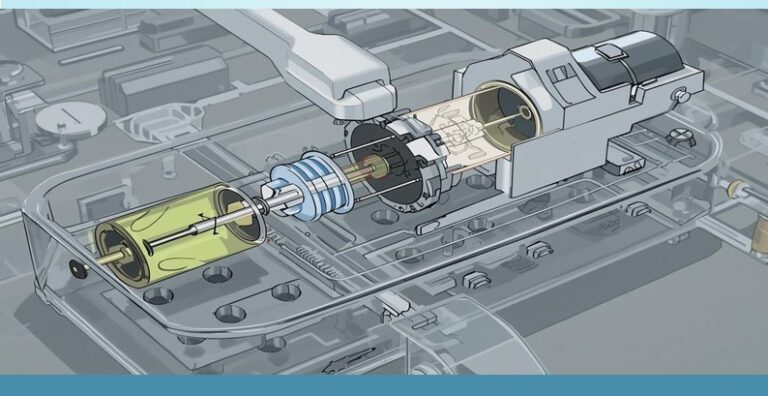
Technical Description This invention relates to a centrifugal microfluidic device design for efficient intracellular delivery through Mechanoporation. Problems Addressed Lacks Portability Inefficient Scalability High Cytotoxicity Complex Manufacturing Limited Precision Ineffective Consistency Tech Features Efficient Cell Delivery Enhanced Throughput Better Portability…